HIPAA Compliance
Speaknosis is committed to complying with the Health Insurance Portability and Accountability Act (HIPAA), which sets the standard for protecting sensitive patient data. We adhere to HIPAA's key principles, including the Privacy Rule, Security Rule, and Breach Notification Rule. A core tenet of our approach is minimizing the data we retain and maximizing control for healthcare providers.
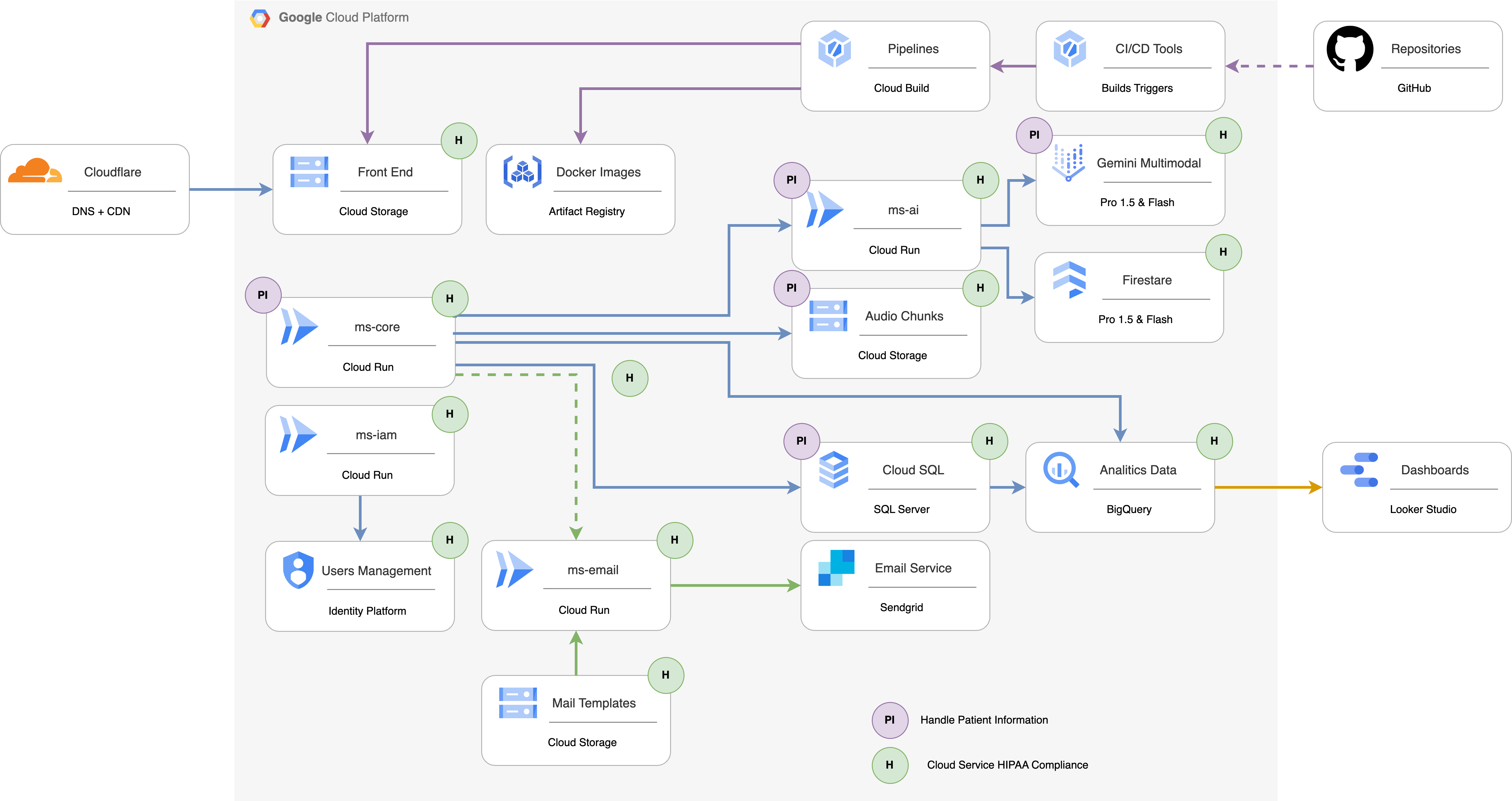
Our HIPAA compliance is reinforced by our use of HIPAA-compliant Google Cloud services and our own internal security measures. Here's how Speaknosis addresses key aspects of HIPAA:
-
Protected Health Information (PHI): Speaknosis prioritizes minimizing the storage of PHI. We de-identify patient data during the transcription process, removing all personally identifiable information while retaining essential clinical data necessary for diagnosis and treatment. Critically, Speaknosis does not store any personal data of the patients. Audio data is stored exclusively within the healthcare provider's designated Google Cloud Storage buckets. This ensures that sensitive patient audio data remains solely under the control of the healthcare provider. Should a healthcare provider opt to utilize our provided storage, stringent data lifecycle policies are in place to automatically delete audio data after 48 hours. This short retention period provides a window for support-related incidents requiring report regeneration while minimizing the amount of sensitive data stored. The following Google Cloud services, which are HIPAA compliant, are involved in handling PHI:
- Cloud Storage
- Cloud Run
- Cloud Kubernetes Engine
- Cloud SQL
- Google Vertex AI (Gemini)
- Google Firestore
- BigQuery
-
Privacy Rule: We adhere to the HIPAA Privacy Rule, which governs the use and disclosure of PHI. We only access and use PHI as necessary to provide our services, and we never share it with unauthorized parties.
-
Security Rule: We comply with the HIPAA Security Rule, which establishes safeguards for protecting the confidentiality, integrity, and availability of electronic PHI (ePHI). Our security measures include data encryption, access controls, security monitoring, and regular security assessments.
-
Breach Notification Rule: In the unlikely event of a data breach, Speaknosis will comply with the HIPAA Breach Notification Rule, promptly notifying affected individuals and relevant authorities.
The following processes and technologies within Speaknosis are designed with HIPAA compliance in mind:
- Secure Audio Capture and Storage: Our secure recording and chunking process, combined with encrypted storage in the healthcare provider's Google Cloud Storage buckets, protects audio data from unauthorized access.
- AI-Powered Transcription and De-identification: Our AI engine transcribes conversations and removes PII, ensuring patient privacy.
- Secure Report Generation and Delivery: Reports are generated and delivered securely to authorized personnel.
- Access Controls and Authentication: Strict access controls and secure authentication methods limit access to PHI.
- Security Monitoring and Auditing: Continuous monitoring and auditing help us detect and respond to security threats.
- Regular Security Assessments and Vulnerability Scans: We regularly assess our system for vulnerabilities and implement necessary security updates.
By combining HIPAA-compliant Google Cloud services with our own rigorous security practices, and by minimizing data retention and maximizing provider control, Speaknosis provides a secure and reliable platform for handling sensitive patient data.